Patched sudo privilege escalation vulnerability CVE-2021-3156


A rather nasty sudo vulnerability has been making news for a couple of weeks now, apparently most of Unix and Unix-like operating systems were affected:
sudo package had heap-based buffer overflow, allowing any user on the system to use sudoedit -s command and become root.
sudo version with CVE-2021-3156 fixed
In most distributions, the updated sudo version is 1.9.5p2.
I have installed macOS update 11.2.1 yesterday that patched the version:
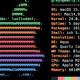
greys@mcfly $ sudo -V
Sudo version 1.8.31
Sudoers policy plugin version 1.8.31
Sudoers file grammar version 46
Sudoers I/O plugin version 1.8.31to the expected 1.9.5p2:
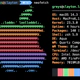
greys@mcfly $ sudo -V
Sudo version 1.9.5p2
Sudoers policy plugin version 1.9.5p2
Sudoers file grammar version 48
Sudoers I/O plugin version 1.9.5p2
Sudoers audit plugin version 1.9.5p2And also updated my CentOS 8 servers, expected version is sudo-1.8.29-6.el8_3.1
root@s:~ # rpm -qa | grep sudo
libsss_sudo-2.3.0-9.el8.x86_64
sudo-1.8.29-6.el8_3.1.x86_64Stay safe!
See Also
- sudo command
- Official sudo website
- CVE-2021-3156
- What does sudo mean?
- Install sudo in Debian
- [macOS update 11.2.1][macos-sudo]
- macOS
- CentOS 8 released