Ubuntu SSH: How To Enable Secure Shell in Ubuntu
SSH (Secure Shell) is possibly the best way to remotely access a Unix system – it’s very secure thanks to automatic encryption of all the traffic, and it’s also quite universal because you can do all sorts of things: access remote command line shell, forward graphics session output, establish network tunnels, set up port redirections and even transfer files over the encrypted session.
Today I’m going to show you how to get started with SSH in Ubuntu.
How To Use Unix Tutorial
IMPORTANT: this article uses shell command examples. Check out the Using Unix Tutorial for details.
Installing SSH server in Ubuntu
By default, your (desktop) system will have no SSH service enabled, which means you won’t be able to connect to it remotely using SSH protocol (TCP port 22). This makes installing SSH server one of the first post-install steps on your brand new Ubuntu.
The most common SSH implementation is OpenSSH. Although there are alternative implementations (closed source solutions and binary distributions maintained by various Unix and Unix-like OS vendors), OpenSSH is a de-facto standard in the secure transfers and connections industry. That’s exactly what you want to install.
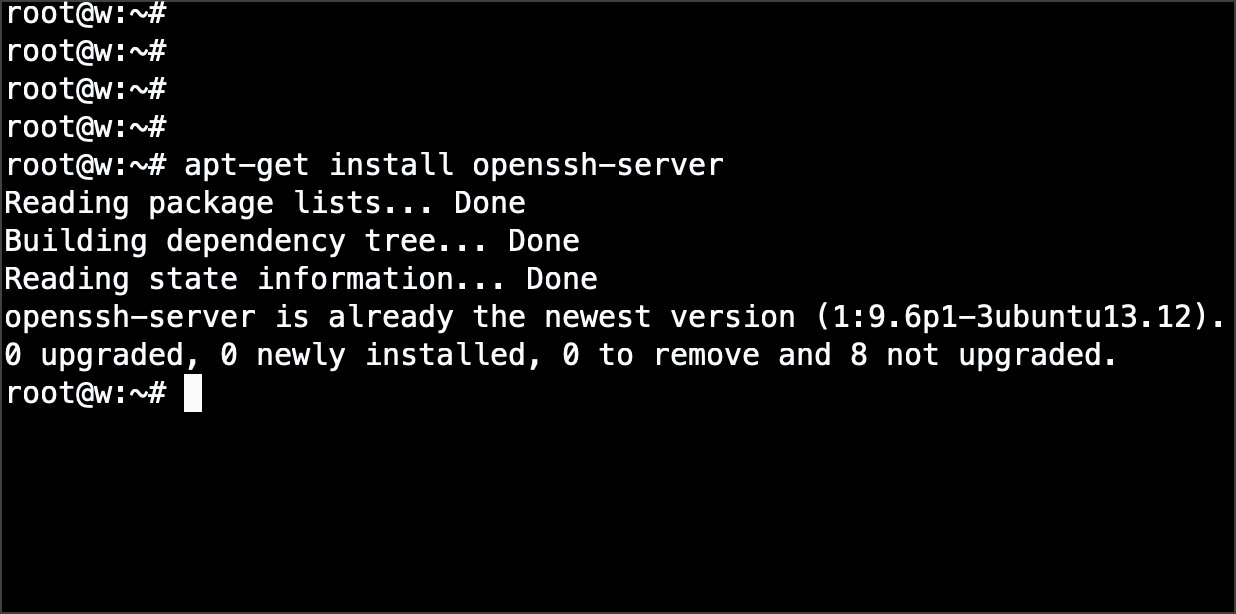
Log in with your standard username and password, and run the following command to install openssh-server package.
You should be using the same username that you specified when installing Ubuntu, as it will be the only account with sudo privileges to run commands as root:
ubuntu$ sudo apt-get install openssh-server [sudo] password for greys: Reading package lists... Done Building dependency tree Reading state information... Done Suggested packages: rssh molly-guard openssh-blacklist openssh-blacklist-extra The following NEW packages will be installed: openssh-server0 upgraded, 1 newly installed, 0 to remove and 75 not upgraded. Need to get 285kB of archives. After this operation, 782kB of additional disk space will be used. Get:1 http://ie.archive.ubuntu.com jaunty/main openssh-server 1:5.1p1-5ubuntu1 [285kB] Fetched 285kB in 0s (345kB/s) Preconfiguring packages ... Selecting previously deselected package openssh-server. (Reading database ... 101998 files and directories currently installed.) Unpacking openssh-server (from .../openssh-server_1%3a5.1p1-5ubuntu1_i386.deb) ... Processing triggers for ufw ... Processing triggers for man-db ... Setting up openssh-server (1:5.1p1-5ubuntu1) ... Creating SSH2 RSA key; this may take some time ... Creating SSH2 DSA key; this may take some time ... * Restarting OpenBSD Secure Shell server sshd [ OK ]
Public and Private keys in SSH
As you can see in the sample output above, the installation procedure created 2 sets of keys – SSH2 RSA keypair and SSH2 DSA keypair. The reason for this is that OpenSSH relies heavily on the public and private key (PPK) infrastructure.
The concept behind PPK is pretty cool: SSH allows you to create keypairs. They are generated to the maximum randomness achievable on your system. Keypairs can be created for your server or for your individual uses.
The idea is that public keys are shared with other servers, and they later can be used as a unique identificator to confirm your true identity. When you’re connecting to another server, it uses your public key to encrypt a short message and the secure session will only be established if on your side you have a private key that allows decrypting the message. No other system or user can decrypt the message because only you would have the private key. That’s why it’s called private – don’t ever share it with anyone.
As an additional security measure, when you’re generating personal keypairs you’ll be asked to supply a passphrase so that even if someone steals your private password they won’t be able to use it without knowing your passphrase.
Verifying your SSH server works
While you’re still on your local desktop session, you can use the ps command to confirm that SSH daemon (sshd) is running:
ubuntu$ ps -aef | grep sshd root 24114 1 0 15:18 ? 00:00:00 /usr/sbin/sshd
Now that you see it’s there, it’s time to try connecting:
ubuntu$ ssh localhost
Since this is the first time you’re trying to connect using SSH, you’ll have to answer yes to the following question:
The authenticity of host 'localhost (::1)' can't be established.RSA key fingerprint is 18:4d:96:b3:0d:25:00:c8:a1:a3:84:5c:9f:1c:0d:a5.Are you sure you want to continue connecting (yes/no)? yes
… you’ll then be prompted for your own password (remember, the system treats such connection request as if you were connecting remotely, so it can’t trust you without confirming your password):
`Warning: Permanently added 'localhost' (RSA) to the list of known hosts.greys@localhost's password:` .. and finally you'll see the usual Ubuntu (Jaunty in this example) banner and prompt: Linux ubuntu 2.6.28-11-generic #42-Ubuntu SMP Fri Apr 17 01:57:59 UTC 2009 i686 The programs included with the Ubuntu system are free software;the exact distribution terms for each program are described in the individual files in /usr/share/doc/*/copyright. Ubuntu comes with ABSOLUTELY NO WARRANTY, to the extent permitted by applicable law. To access official Ubuntu documentation, please visit:http://help.ubuntu.com Last login: Fri May 15 15:18:34 2009 from ubuntu ubuntu$
That’s it, providing you have your networking configured and you know your IP address or hostname, you can start connecting to your Ubuntu box from remote systems, using the same command. Enjoy!